| University | Nanyang Polytechnic (NYP) |
| Subject | Network Security |
Network Security – Practical Assignment (30 marks)
This is an individual assignment. You are required to carry out the following two tasks as part of this assignment that carries 30% towards your final score.
Note: Plagiarism is a serious offence that may lead to failure of this module. Please be assured your independent work is much recognized, appreciated and awarded.
Submission Details
The task-1 requires you to save the packet tracer file (.pkt) as “Admin No_Name.pkt” and the task2 as a word document in “Admin No_Name.doc”. Zip them together and upload into Bright Space under the submission tab. Due date is 8th February 2026 2359 Hrs. Any late submissions will be handled by NYP late submission policy i.e. even by a second late from the due date, grade capped at 50% for up to five days and anything beyond will be awarded ZERO.
Task 1 (20 marks)
To design and implement a secured network infrastructure on packet tracer using the base packet tracer file provided (without any configuration, only physical topology provided) as per the scenario and requirement listed below. Begin with a network design of IP Addresses as per the host requirement below. You may select an appropriate private IP block for your network design, may follow FLSM or VLSM and public IP addresses for ISP/Internet devices.
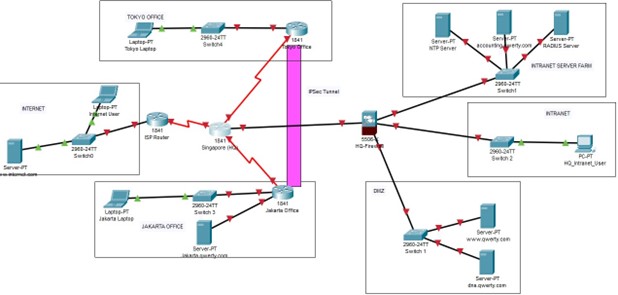
Scenario
You are the Security Consultant of ‘QWERTY Company’ that offers online social services to its clients. They have their HQ at Singapore, branch offices at Jakarta and Tokyo.
General Requirement
To configure the secured network infrastructure such that:
- HQ and their branch offices each have an administrator. They have accounts created locally on the respective routers as “HQ_Admin, Tokyo_Admin and Jakarta_Admin” with secret password as ‘admin_no’g. ‘123456D’ o All the devices to have hostnames as ‘admin_no_location’ E.g. 123456D_Branch o All the devices to have enable passwords as ‘admin_no_enable’ E.g. 123456D_enable’
- All the routers accept only two (2) virtual lines through SSH and are authenticated (AAA) through Radius server located at INTRANET_SERVER_FARM. In case radius server is not available, local accounts should be used for AAA. Radius Server should have a user account ‘Radius_Admin’ with password as’admin_no’. Telnet, Console and Auxiliary connections not to be allowed.
- Passwords used on all the routers are encrypted when displayed (Eg.sh run config) All the routers are time-synchronized with the NTP server.
NTP Parameters Table
| NTP Server | Key | MD5 Password |
| xx.xx.xx.xx | 1 | SITNetSec |
- The entire network (except ISP Router) must have OSPF as the routing protocol with Type 2 authentication with the key as “Admin_no_MD5”.
- Hello and Dead intervals between all routers are set as 10 and 15 seconds respectively across all routers.
- Note there is no direct connectivity between Tokyo and Jakarta offices. IPSec site-to-site VPN is to be configured between Tokyo and Jakarta offices. Use the parameters as appropriate and document them.
- Each network to have at least one PC connected to test connectivity.
- In terms of access to servers, propose and implement the following:
o Access to the Radius Server to be limited (to only HQ/Jakarta/Tokyo offices) o Access to other servers hosted at HQ/Jakarta to be limited with the specific port numbers as applicable.
HQ @ Singapore
- The HQ consists of three LANs namely INTRANET, DMZ and INTRANET SERVER FARM as detailed below and boxed up in the topology.
- HQ hosts a LAN (INTRANET) that consists of three departments across three floors namely HR (7 staff), Accounting (5 staff) and Management (4 staff) and all the staff are provided with only desktops. i.e. You need to plan for a single subnet that consists of HR, Accounting and Management departments.
- HQ also has server farm (DMZ) that hosts web server (www.qwerty.com) and DNS server (dns.qwerty.com). Both Internet and Intranet users to have secured access to the web server and DNS server.
- Propose a security plan given that there is a budget to buy an ASA5506/ASA5505 (select an appropriate firewall model) to secure the network. You may use techniques like security levels, security zones, and ACLs.
- All the company users to have only secured web access to accounting.qwerty.com that is part of INTRANET SERVER FARM
- Port Security is to be enabled as per the connectivity shown in the packet tracer started file and unused ports must be administratively disabled. Any breaches must require administrator’s action.
- Singapore HQ Router has connectivity to the ISP and the required routing (Hint: Default route) is to be configured for all the devices to access Internet through this link. ISP uses router model 1841 and uses 64K serial link (DCE) to connect to the HQ. All company users connect through HQ router for Internet access.
TOKYO Office
- The Tokyo office has 6 staff members with laptops.
- Tokyo office connects to HQ for secured web access to accounting.qwerty.com.
- Tokyo office connects over IPSec site-to-site VPN with Jakarta office to access Jakarta.qwerty.com over only HTTPS.
- Tokyo Router connects to Radius Server @ INTRANET SERVER FARM for authentication as per the general requirement above.
- Tokyo Router synchronises its clock with NTP Server @ INTRANET SERVER FARM.
- Port Security is to be enabled on Switch-4 with the maximum of 3 MAC addresses and rest of the unused ports to be administratively disabled. Any breaches do NOT require administrator’s action.
JAKARTA Office
- The Jakarta Office has 18 staff members with laptops.
- JAKARTA office connects to HQ for secured web access to accounting.qwerty.com.
- Tokyo office connects with Jakarta over IPSec site-to-site VPN to access Jakarta.qwerty.com over only HTTPS. HQ users also have access to Jakarta.qwerty.com over HTTPS.
- Port Security is to be enabled on Switch-3 with the maximum of 2 MAC addresses and rest of the unused ports to be administratively disabled. Any breaches do NOT require administrator’s action.
Task 2 (10 marks)
Write a detailed report that covers the following points:
- Your considerations for the network IP address and FLSM/VLSM design.
- Tabulate (as per the table below) all the IP addresses used per location basis including the mask chosen. Do note that your choice of mask should be closer to the number of host machines required in the subnet as per the requirement in order not to waste any IP addresses.
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
- Your considerations, justification and explanation of the security measures implemented at every location.
- Document the verification/test results by attaching screenshots where applicable.
- Any assumptions made must be stated clearly under a separate section “Assumptions”.
- Attach the current configuration of every device that you have implemented as annex.
Assignment Rubrics
| Individual | Excellent (A) | Very Good (B) | Good
(C) |
Satisfactory (D) | Unsatisfactory (F) |
| Task – 1 Design and implementation of secured network infrastructure based on stated requirement | All requirements working seamlessly and wellimplemented.
|
Most requirements working and wellimplemented.
|
Some requirements working and generally wellimplemented.
|
Some
requirements are incomplete or erroneous.
|
Requirements are mostly incomplete or erroneous.
|
| Task – 2
Detailed report on the network IP design, considerations, justifications for different security requirement and justifications.
|
Report is well organized and written. All information clearly explained and conveyed.
Good use of language, with no grammar and spelling mistakes.
|
Report is organized and written. Most information clearly explained and conveyed.
Good use of language, with few grammar and spelling mistakes. |
Report is somewhat organized and written. Some information clearly explained and conveyed.
Good use of language, with some grammar and spelling mistakes. |
Report is badly organised and written and lacking clear explanation of information.
Poor use of language, with many grammar and spelling mistakes.
|
Report is unclear, confusing, and badly organized/written.
Poor use of language, with too many grammar and spelling mistakes that leads to content being incomprehensible. |
Struggling with Network Security Practical Assignment at NYP?
Native Singapore Writers Team
- 100% Plagiarism-Free Essay
- Highest Satisfaction Rate
- Free Revision
- On-Time Delivery
Many Nanyang Polytechnic (NYP) students struggle with the Network Security Practical Assignment due to complex Packet Tracer configurations, strict security requirements, and detailed documentation expectations.If designing a secured network with AAA, OSPF, IPSec VPN, firewall rules, and VLSM/FLSM planning feels overwhelming or time is limited, there’s no need to worry. Singapore Assignment Help provides networking assignment help Singapore aligned with NYP practical rubrics and submission guidelines. For trust and confidence, you can also review our expert-written assignment samples before ordering personalised support for your Network Security coursework.
Looking for Plagiarism free Answers for your college/ university Assignments.
- GPS2301 Interventions & Strategies in Special Needs Education Assignment 2026 | TP
- PSB5045EE Analog and Digital Electronics (ADE) Assignment Questions 2026
- GSS502 Global Security, Strategy and Leadership Tutor-Marked Assignment – 01, January 2026 Presentation
- MGT567 Strategic Human Capital and Talent Management End-of-Course Assessment Questions Jan 2026 | SUSS
- FMT321 Fire Safety & Engineering Tutor-Marked Assignment – Two, January 2026 Presentation
- PSB7006CL Entrepreneurship Business Plan Assessment Coursework 1 2026 | PSB Academy
- B3029C Career Counselling Project Coursework Assessment 2026 | RP
- MTD115 Fundamentals of Digital Photography Tutor-Marked Assignment Jan 2026 Presentation
- HS6433 Health Promotion and Counselling Assignment 2026 | NYP
- BCEC002 Business Economics Individual Assignment Brief 2026 | Temasek Polytechnic

