| University | University of Wollongong (UOW) |
| Subject | CSCI368: Network Security Assignment |
1. Consider the following key exchange protocol which is a variant of the Diffie-Hellman protocol. Each user P has a secret key sk_P=x_P and public key pk= gx_P mod p.
1: A B: gr_A mod p
2: B A: gr_B mod p
In the protocol, r_A and r_B are randomly chosen in each session by A and B. The shared key for communication is defined as K = gr_Ax_B + gr_Bx_A mod p.
a) Show the key derivation formulas of User A and User B (i.e., how does each
user compute the shared key?)
c) Does the protocol provide Forward Secrecy? Justify your answer.
Stuck with a lot of homework assignments and feeling stressed ? Take professional academic assistance & Get 100% Plagiarism free papers
2. Two questions related to the A1. For each question, you should use one sentence to highly summarize the problem (1 mark) and then use 1-3 sentences to explain it.
a)Briefly describe the issue when the adversary is able to know the secret key sk_s.
b)Briefly describe the problem when Alice’s algorithm always uses the same r for secure communications.
3. Consider the following certificate mechanism.
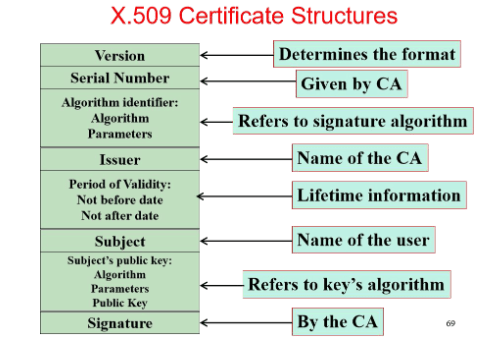
The CA generates the signature but the message to be signed excludes “Refer to Key’s Algorithm”. Describe how the adversary can launch the MITM attack on TLS protocol in the real world. You should start with the application scenario that user Alice wants to access the web resources manager by the web server Bob. You should use at least three steps to highly describe this kind of attack.
Hire a Professional Essay & Assignment Writer for completing your Academic Assessments
Native Singapore Writers Team
- 100% Plagiarism-Free Essay
- Highest Satisfaction Rate
- Free Revision
- On-Time Delivery
Are you ready to navigate the intricacies of Network Security? Our tailored Dissertation Writing Services Singapore awaits CSCI368 students in Singapore. Dive into the complexities of securing computer networks with confidence through our expert Assignment Help Online.
Looking for Plagiarism free Answers for your college/ university Assignments.
- BM0973 BCRM Assignment: Genting Highlands Case Study for Crisis Response and AI-Supported Recommendations
- AC0779 Strategic Management Assignment Essay: Key Activities & Importance in Dynamic Healthcare Settings
- ComfortDelGro Organisational Design Assignment Report: ESG Alignment with UNGC Principles & Sustainability Strategy
- Bomb Threat Management Assignment: Incident Response Plan for High-Risk Facilities in Singapore
- Security Concept Plan Assignment Report: International School Campus Protection Strategy at Jurong East
- CM3065 Intelligent Signal Processing Assignment Report: Midterm Exercises on Audio Captcha, Steganography & Speech Recognition
- BUS306 Risk Assessment Case Study: Outback Retail Ltd Audit Strategy and Substantive Testing Plan
- PSB6013CL Digital Marketing Strategies Project: Exploring Consumer Purchase Intentions in the Fashion E-Commerce Industry
- FinTech Disruption Assignment Report: Case Study on Digital Transformation in Financial Services Industry
- Strategic Management Assignment : Netflix vs Airbnb Case Analysis on Competitive Strategy and Innovation

